Some things from a security audit that were brought up and can effect many sites by default.
Deprecated Encryption Protocol & Cipher
Test:
nmap --script ssl-enum-ciphers \
-p 443 \
website.com
Alternatively, and more in-depth: https://www.ssllabs.com/ssltest/
Result:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-09 09:45 BST
Nmap scan report for [redacted]
Host is up (0.023s latency).
Other addresses for [redacted] (not scanned): [redacted]
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| TLSv1.2:
| ciphers:
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256-draft (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256-draft (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| compressors:
| NULL
| cipher preference: client
|_ least strength: C
Nmap done: 1 IP address (1 host up) scanned in 2.37 seconds
Result:
The systems support a deprecated TLS encryption protocol and associated cipher.
The cryptographic protocols and ciphers supported by some applications can undermine the secure communication between the server and the client.
Remediation:
The easy way, following https://httpsiseasy.com/
- Disable the use of TLS v1.0, TLS v1.1 encryption protocol
- Disable the use of DES encryption cipher.
Basically enabling TLS 3, and setting minimum TLS version to TLS 1.2. (TLS 1.3 support is good but not massive).
Go to SSL/TLS -> Edge Certificates
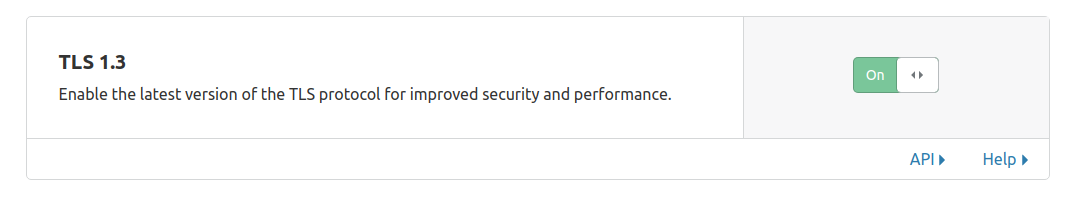
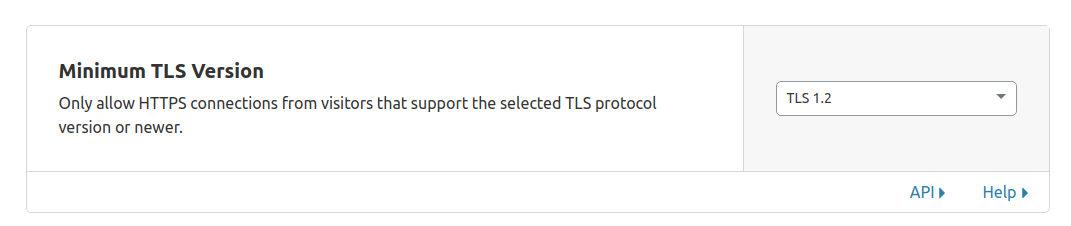
Now run the script again with these changes:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-09 10:19 BST
Nmap scan report for [redacted]
Host is up (0.019s latency).
Other addresses for [redacted] (not scanned): [redacted]
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256-draft (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256-draft (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| compressors:
| NULL
| cipher preference: client
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 1.96 seconds
Information Disclosure
Reason:
Information about the backend server and associated system is exposed through error disclosure. This may allow an attacker to perform tailored attacks against such components if found vulnerable.
Result:
Server responses may reveal information about the version of the backend system components.
Remediation:
Edit the server version value from the response header and create a custom error page, so that should any error occur, the custom page will be displayed rather than the default error messages.
Source:
Add to top of a config file, e.g.:
/etc/apache2/sites-available/000-default.conf
ServerTokens Prod
ServeSignature Off
More info on:
apache2ctl configtest and systemctl reload apache2 if all good.
Adding extra security headers.
Source:
sudo a2enmod headers
sudo systemctl restart apache2
sudo apache2ctl configtest
Within the <VirtualHost> directive of a config file, e.g.:
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains;"
Header always set X-Frame-Options "deny"
Header always set X-Content-Type-Options "nosniff"
Header always set Referrer-Policy "same-origin"
More info on:
Summary of suggested headers from securityheaders.com:
Strict-Transport-Security- HTTP Strict Transport Security (HSTS) is an excellent feature to support on your site and strengthens your implementation of TLS by getting the User Agent to enforce the use of HTTPS.
- Recommended value
Strict-Transport-Security: max-age=31536000; includeSubDomains.
Content-Security-Policy- Is an effective measure to protect your site from XSS attacks. By whitelisting sources of approved content, you can prevent the browser from loading malicious assets.
X-Frame-Options- Tells the browser whether you want to allow your site to be framed or not. By preventing a browser from framing your site you can defend against attacks like clickjacking. Recommended value
X-Frame-Options: SAMEORIGIN.
- Tells the browser whether you want to allow your site to be framed or not. By preventing a browser from framing your site you can defend against attacks like clickjacking. Recommended value
X-Content-Type-Options- Stops a browser from trying to MIME-sniff the content type and forces it to stick with the declared content-type. The only valid value for this header is
X-Content-Type-Options: nosniff.
- Stops a browser from trying to MIME-sniff the content type and forces it to stick with the declared content-type. The only valid value for this header is
Referrer-Policy- Is a new header that allows a site to control how much information the browser includes with navigations away from a document and should be set by all sites.
Feature-Policy- Is a new header that allows a site to control which features and APIs can be used in the browser.
Expect-CT- Allows a site to determine if they are ready for the upcoming Chrome requirements and/or enforce their CT policy.
Verify the results:
$ curl --include --location --head website.com
HTTP/2 200
date: Tue, 09 Jun 2020 10:05:19 GMT
content-type: text/html; charset=UTF-8
set-cookie: __cfduid=[redacted]; expires=Thu, 09-Jul-20 10:05:19 GMT; path=/; domain=[redacted]; HttpOnly; SameSite=Lax
strict-transport-security: max-age=63072000; includeSubdomains;
x-frame-options: deny
x-content-type-options: nosniff
referrer-policy: same-origin
cache-control: no-cache, private
cf-cache-status: DYNAMIC
cf-request-id: [redacted]
expect-ct: max-age=604800, report-uri="https://report-uri.cloudflare.com/cdn-cgi/beacon/expect-ct"
server: cloudflare
cf-ray: [redacted]
Harder to see, but can try and come up with some screenshots for this.
Some nmap things that might be interesting.
yq: Command-line YAML/XML processor - jq wrapper for YAML and XML documents
sudo apt install jq
pip3 install yq
nmap -Ox out.xml ..
cat out.xml | xq '.nmaprun.host.ports.port.script'